Optimizing Your AI-SOC: A Practical Guide to Offensive Validation and Tuning
- Gurucharan R
- Sep 16, 2025
- 3 min read
Mid-sized SOC teams often deploy AISOC platform for better security posture, but don’t always know how to truly measure and optimize these systems. Here is a concise guide for defenders on using offensive security (red/purple team) methods—plus an actionable, 6-week plan—to maximize AI-driven SOC automation and response.
Where Mid-Sized SOCs Fall Short with AISOC
Alert Overload: Analysts face thousands of daily alerts, most of which are false positives, leading to alert fatigue and slow incident response.
Resource Constraints: Building a 24/7 SOC is expensive, and most mid-sized organizations can’t staff full coverage.
AISOC Gaps: Teams often “set and forget” AI detection, rarely validating its accuracy or coverage against realistic attacks.
Integration: Siloed tools and a lack of workflow automation mean threats slip through, and SOCs can’t leverage full AI potential.
Using Offensive Security to Test AI / Purple teaming: collaborative drills between defenders (SOC/Blue team) and attackers (Red team) is ideal for testing AI-powered detection and response systems:
Simulate Real Attacks: Run MITRE ATT&CK scenarios with tools like Metasploit, Atomic Red Team, or Caldera to mimic real adversaries.
Measure Detection: Track how the AI responds: Does it miss attacks? Over-alert? Auto-contain threats?
Continuously Tune: Use insights from these exercises to improve detection rules, automate playbooks, and cut manual work.
Intuitive SOC Automation Hub

How AI Automation Quickly Reduces SOC Workload:
Automation Area | What AI Does | Fastest Wins |
Alert Triage | Auto-classifies + ranks alerts | Fewer false positives |
Threat Hunting | Proactively hunts threats 24/7 | Early, automatic detection |
Incident Response | Runs containment & recovery steps | Rapid quarantine, auto-tickets |
Behavioral Analytics | Flags anomalous user/entity actions | Insider threats, account abuse |
Compliance Monitoring | Auto-generates reports, enforces policies | Less manual reporting |
Vulnerability Management | Prioritizes, automates patching | Patches high risks first |
6-Week Action Plan - Accelerated Rollout
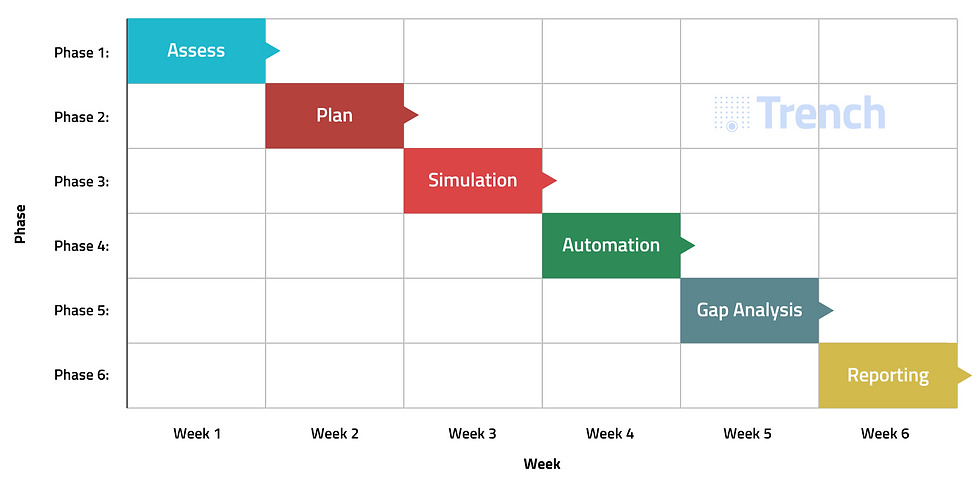
Week 1: Baseline Assessment
Inventory current SOC controls and existing workflows
Measure false positive rate, mean time to respond (MTTR), top pain points
Week 2: Scenario Design
Plan focused purple team exercises for three high-priority attack types:
Credential abuse (e.g., password spraying)
Phishing with malware delivery
Privilege escalation
Week 3: Offensive Simulation
Run targeted red/purple tests using selected tools
Log AI-powered detection, response, and gaps
Week 4: Automation Sprint
Enable or refine SOAR playbooks in the AI platform for top detection end-to-end use cases
Test auto-containment and notification flows
Week 5: Gap Remediation
Address missed detections or slow responses
Retrain AI models/rules as needed with your feedback prompts
Fine-tune incident workflows for speed and accuracy
Week 6: Review & Report
Measure improvement in alert volumes, noise reduction, response time, high quality rules created and actions taken
Deliver summary dashboard and track the overall automation coverage across your attack surface and workflows
Sample Use Case Spotlight
Phishing Response Automation: AI detects the threat, quarantine the malicious email, revokes session token, notifies the SOC analysts automatically with the required evidences and response action plan
Insider Threat Detection: SOC receives alert for abnormal access after hours, AI flags risky user, triggers containment without manual review.
Malware analysis: When EDR detects malware, the AI agent should investigate the alert for malicious activity. If confirmed malicious, the agent should contain the endpoint and communicate the evidence and response plan in the collaboration channel such as Slack, Teams.
Vulnerability Patching: AI identifies and auto-patches critical vulnerabilities prioritized by real-world exploit likelihood.
Best Practices
Iterate often: Repeat purple team tests monthly, adjusting AI and playbooks.
Automate feedback: Link test results directly to AI agent capabilities and your priority scenarios.
Focus on impact: Tackle the top pain points (alert fatigue, slow response and high quality detections) first for fastest return on effort.
By blending offensive security with focused AI automation, SOC teams cut noise, reduce manual work, and react faster without adding costly staff or tools.
At Trench Security, we always advocate for organizations to implement offensive validation. Our onboarding process for Trench’s AI-native capabilities includes this offensive validation plan as a key success criterion. This is crucial for both the organization and AI-native platform vendors like us, ensuring successful outcomes regarding automation coverage and organization-specific KPIs by the end of the deployment cycle.





Comments